Meet the Magecart hackers, a persistent credit card skimmer group of groups you’ve never heard of
There have been few hacker groups that have been responsible for as many headlines this year as Magecart.
You might not know the name, but you probably haven’t missed their work — highly targeted credit card skimming attacks, hitting Ticketmaster and British Airways, as well as consumer electronics giant Newegg and likely many more sites that have been silently hacked to scrape consumer credit card data at the checkout.
Nobody knows those attacks better than Yonathan Klijnsma, a threat researcher at security firm RiskIQ, who’s been tracking Magecart for more than a year.
In a new report published with risk intelligence firm Flashpoint, Klijnsma has exposed the inner workings of the hackers — a group of groups, rather than a single entity — all with different modus operandi and targets, which he described as a “thriving criminal underworld that has operated in the shadows for years.”
“Magecart is only now becoming a household name,” the researcher said.
Chief among Klijnsma’s findings is that there are at least six distinct groups operating Magecart skimming scams, each taking their own approach. Group 1 began as early as 2014 by targeting thousands of sites with attacks and single-use servers for hosting the malware and storing the collected data, while Group 2 and Group 3 expanded their reach and honed their attacks to hook their card skimming malware on a greater range of payment providers. Group 4 took the bulk of the victims — more than 3,000 sites hacked — with its scattergun approach, grabbing as many cards as it could from as many sites as it could.
The groups have been going where the money is — breaking into websites using known server vulnerabilities, injecting card payment skimming code and siphoning off credit card numbers, names and security codes on an attacker-controlled server, often for months at a time.
If they get caught, they just move on to their next victim.
Magecart’s most high-profile victims were the work of Group 5, which carried out supply chain attacks by hitting third-party code providers — like customer service chat boxes — that are installed on thousands of sites and carrying the group’s malware with it, expanding the group’s reach on a massive scale. It was Group 5 that RiskIQ blames on targeting many of Ticketmaster’s global sites. Group 6, meanwhile, also began highly selective attacks that only targeted major players — including British Airways and Newegg.
Between the half-dozen groups that RiskIQ has identified so far, at least 6,400 sites have been affected.
And that’s just the start.
Once a steady stream of credit card numbers come in, the hackers will sell the data — often on the dark web, making it easier to hide their activities from the law.
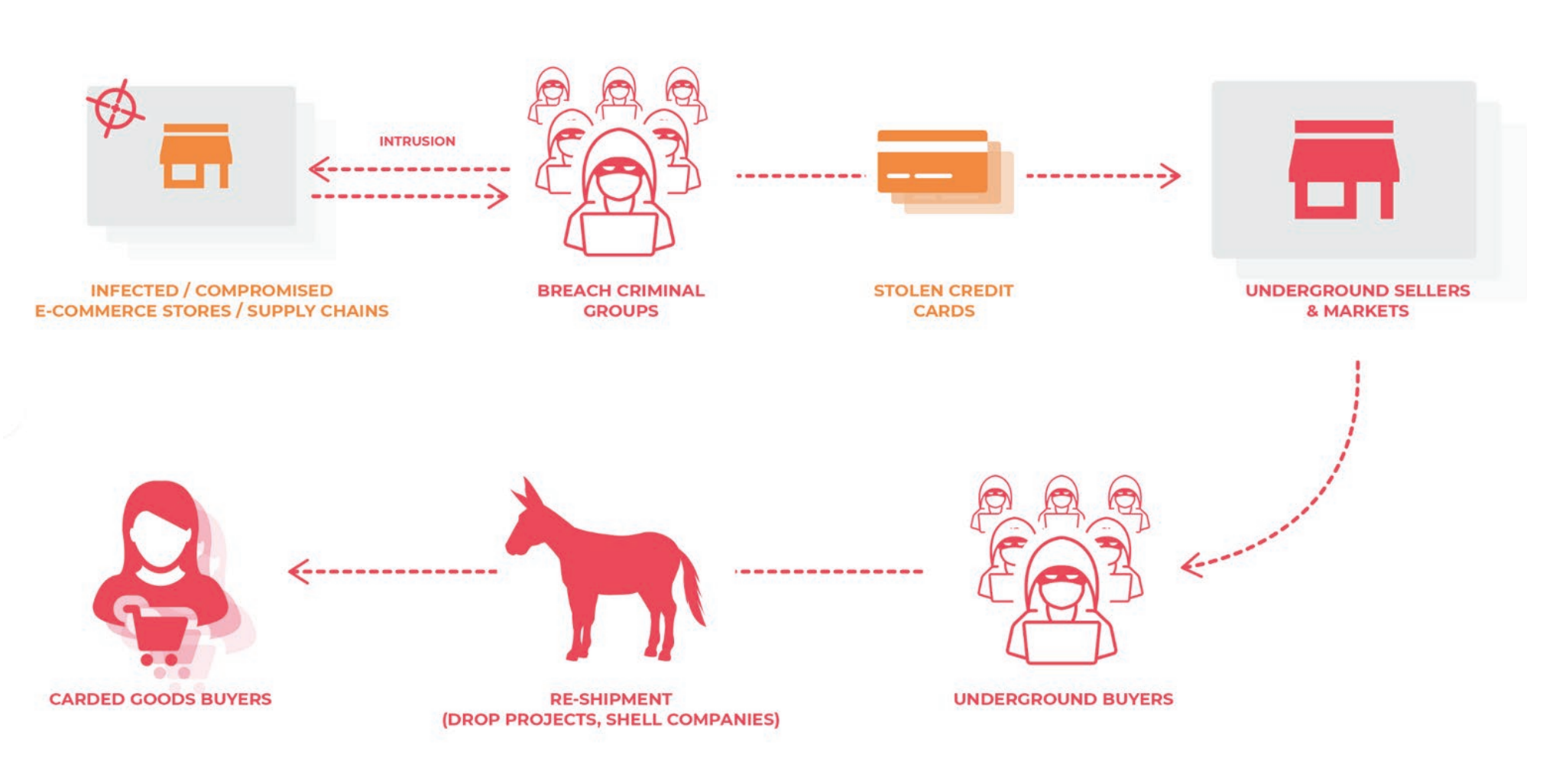
Magecart’s credit card skimming cycle. (Image: RiskIQ/Flashpoint)
Klijnsma warned that there will be many more card skimming groups and many more websites affected — larger and lesser-known sites alike that have yet to be discovered.
Case in point: Earlier this year, little-known New Jersey-based electronics retailer TechRabbit disclosed a data breach. Like so many other sites, it went largely unnoticed — except, upon closer inspection, the breach had all the hallmarks of Magecart. Willem de Groot, a security researcher cited in the Magecart report, confirmed on Twitter — and independently verified by TechCrunch — that the site had been hit again months later.
We reached out to the company’s chief executive, Joel Lerner, to inform him of the card skimming malware. “Who is TechCruch [sic] and what do you know about TechRabbit?” he said.
After several emails back and forth, including a screenshot sample of the malware on the site’s checkout pages, he expressed concern but stopped responding.
Klijnsma conceded that although his research has given an unprecedented insight into how the Magecart groups work, “that doesn’t mean we will be able to spot every instance and every attack,” he said. There are likely many more sites affected by card skimming malware — as of yet undetected. “We’d like to call on the industry and everyone who encounters these attacks to help take it down,” he said.
To combat the threat from Magecart, RiskIQ and other cybersecurity firms can sinkhole domains associated with Magecart infrastructure, pulling them offline and out of operation.
Klijnsma said it requires a layered approach — like website owners improving their security with security patches and segregating servers. “You don’t catch this with just one security control but rather you stack them and try to catch it at at least one of these steps,” he said.
“Basically any vector is game among these groups with some groups utilizing all of them to reach their goal of breaching a target,” he said.

