Thousands of industrial refrigerators can be remotely defrosted, thanks to default passwords
Security researchers have found thousands of exposed internet-connected industrial refrigerators that can be easily remotely instructed to defrost.
More than 7,000 vulnerable temperature controlled systems, manufactured by U.K.-based firm Resource Data Management, are accessible from the internet and can be controlled by simply plugging in its default password found in documentation on the company’s website, according to Noam Rotem, one of the security researchers who found the vulnerable systems.
Many of these vulnerable units are found in industrial refrigerators in restaurants, hospitals, and supermarkets and grocery stores from the U.K., Ireland, and as far away as Sweden, Germany and China. The researchers also found a pharmaceutical company in Malaysia and a cooling facility in Germany.
Defrosting the refrigerators could lead to untold water damage, financial losses, and the destruction of inventory. In the case of high-value industries, that could amount to hefty losses.
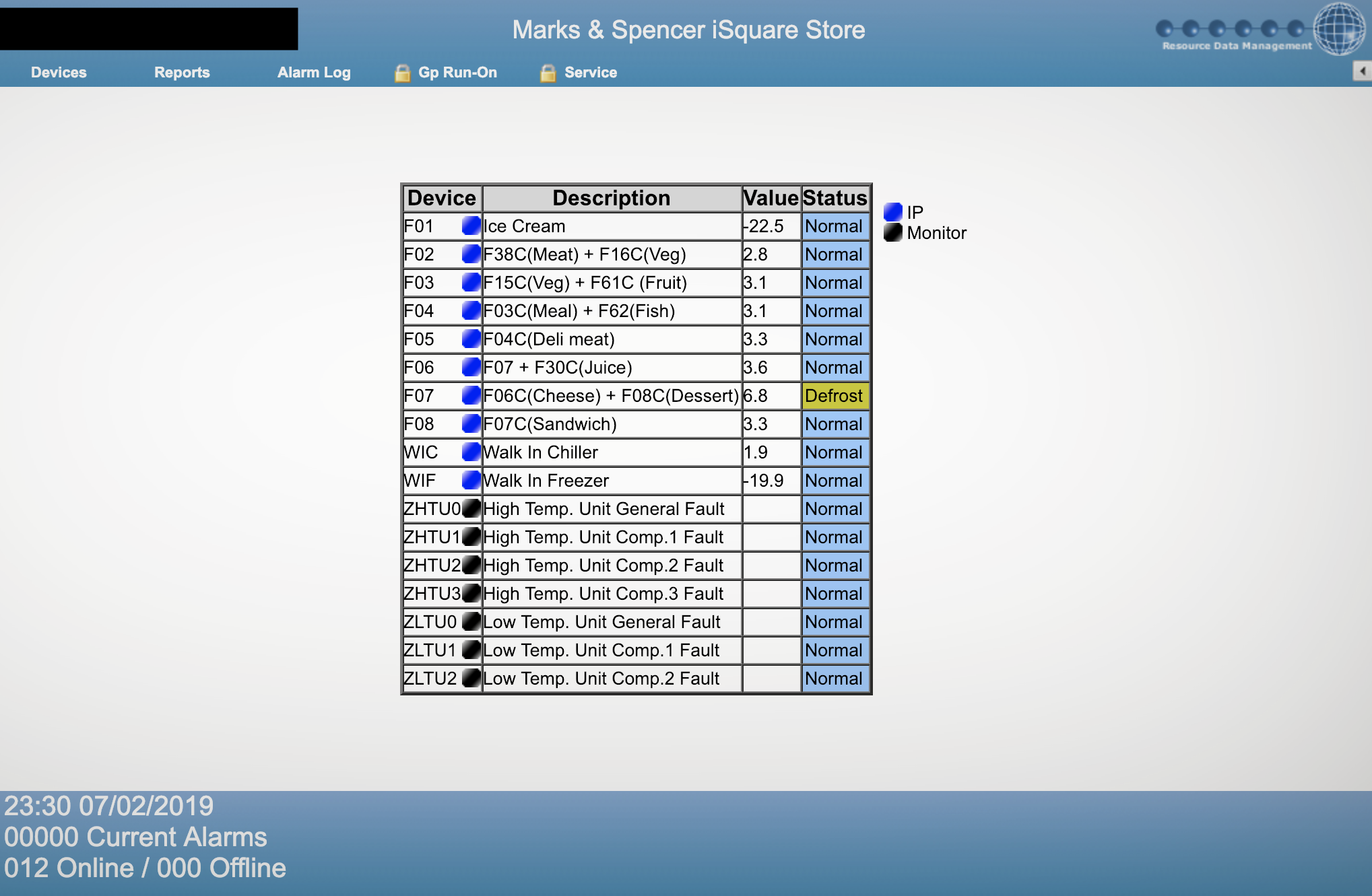
The web interface of an industrial freezer at a Marks & Spencer in Hong Kong. (Image: TechCrunch)
“The systems can be accessed through any browser,” said Rotem in his write-up. shared with TechCrunch before his public disclosure. “All you need is the right URL, which as our tests show, isn’t too difficult to find.”
Rotem said defrosting a machine takes only a “click a button and enter the default username and password,” both of which are near-universal across the company’s devices. TechCrunch found several hundred refrigerators on Shodan, a search engine for publicly available devices and databases, confirming the researchers’ findings, but did not use the credentials as doing so would be unlawful.
It’s also possible to modify user settings, alarms, and other features on the exposed devices, said Rotem.
In an email, a representative from Resource Data Management said: “We clearly state in our documentation that the default passwords must be changed when the system is installed.” However, the change isn’t mandatory. According to Rotem, many device owners don’t bother. The company also distanced itself from its own security practices. “We have no control over how our systems are set up by the installer and we suggest your article is directed at the users and installers of our equipment,” the representative said. “We will inform owners that we have new software available with new functions and features but ultimately it is up to them to request an upgrade.”
The company said it will write to all its known customers “reminding them of the importance of changing the default user names and passwords.”
Starting next year, California will ban internet-connected devices manufactured or sold in the state if they contain a weak or default password that isn’t unique to each device.
February 08, 2019 at 02:55AM

